Security is a core component of any information governance program. Defining how access to content will be controlled is a key decision. There are two popular methods for implementing a security strategy, Zero Trust and Trust but Verify. Often, those two views are considered mutually exclusive, but are they? This post provides a high-level overview of these two approaches and discusses how they may complement one another.
The Difference Between Information Security Approaches: Zero Trust and Trust but Verify
Often, the debate between a ‘Zero Trust’ and Trust but Verify’ approach is used in the context of network infrastructure. For example, in a Gartner post Susan Moore writes:

The term “Zero Trust” is widely abused in security product marketing. However, it is useful as a shorthand way of describing an approach where implicit trust is removed from all computing infrastructure. Instead, trust levels are explicitly and continuously calculated and adapted to allow just-in-time, just-enough access to enterprise resources.
Adding to that thought, Gartner Distinguished VP Analyst Neil MacDonald states,
“Zero trust is a way of thinking, not a specific technology or architecture” [1]
Zero Trust advocates maintain that no one should have access to information unless they have a well-defined business requirement. Even then, access may be minimal (a concept referred to as least privilege). To be fair, this approach is historically the way organizations have approached access to information.
In the late 1990’s I worked as an IT consultant for a CPA firm. At that time, much of their client confidential information was still paper-based. Gaining access to one of those files required that a requisition form be completed, approved by a senior partner, and presented to a file clerk who would retrieve the file and ask for yet another signature on a sign-out document. Although tedious and time-consuming, the process was effective, and client information was demonstrably protected.
[1] https://www.gartner.com/smarterwithgartner/new-to-zero-trust-security-start-here/
Top Two Information Security Approaches
1) Zero Trust
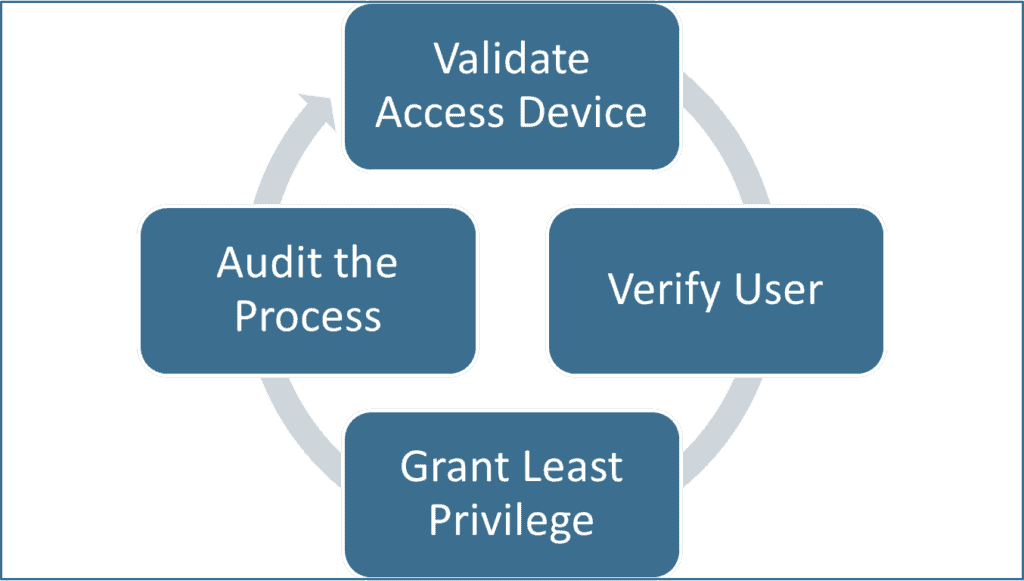
Though technology has evolved (e.g., network shares or SharePoint has replaced file rooms), a Zero Trust model still primarily operates under the same assumption; every attempted access to information is hostile until established otherwise.
Most Zero Trust solutions utilize some type of registration process to validate a device then require employees to use a multi-factor authentication (MFA) process to gain access to an application or other corporate information. Vendors who promote these solutions often tout them as more secure and convenient for end-users since they do not have to utilize long, complex passwords.
2) Trust but Verify
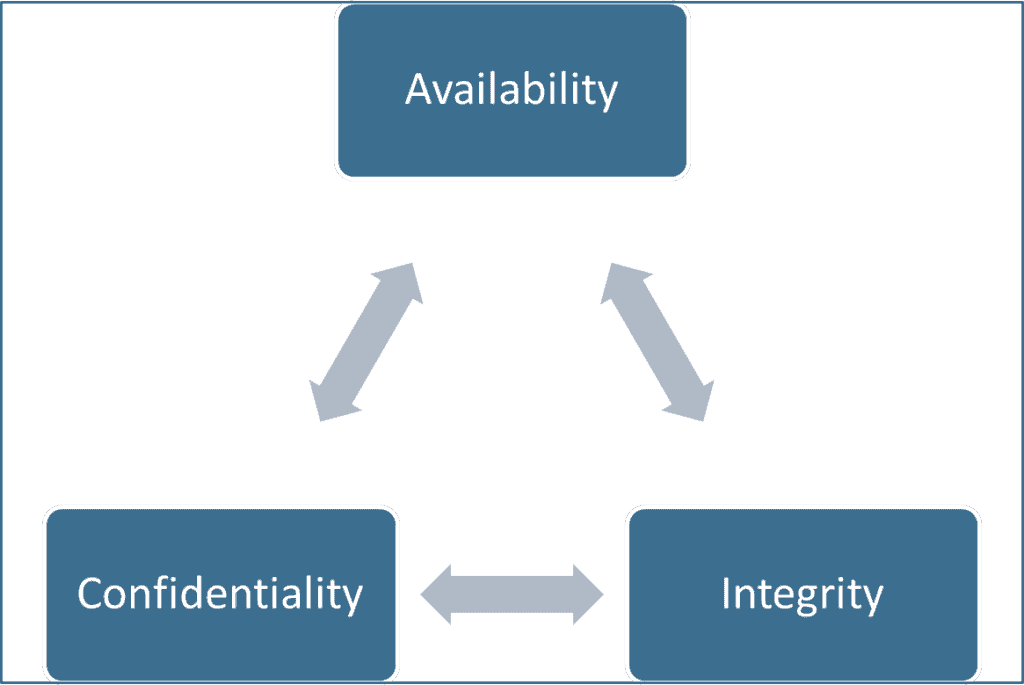
In contrast, a ‘Trust but Verify’ approach to security is based on the tenant that employees have the right to decide what information they need access to and how much risk to accept. Often, these rights are expressed as a triad comprised of availability, integrity, and confidentiality. This implies employees are granted unrestricted access (availability) with the understanding they are expected to act responsibly (integrity) and reasonably protect those assets (confidentiality).
Of course, those decisions must be audited to hold employees responsible and accountable for their decisions. If the audits reveal a problem, appropriate corrective action (for example, additional employee training) is taken. Proponents of this approach argue that the audit process is the key point since that ensures compliance.
Which Information Security Approach is Better?
Reliance on a Zero Trust initiative is undoubtedly a sound decision to secure your network infrastructure or validate the authenticity of the individuals attempting to access network resources. Still, many organizations find that least privileged access to content is too restrictive for today’s fluid business environment. Trust but Verify alone provides information workers with the unfettered access they need to be nimble but can expose the infrastructure to excessive risk.
At Gimmal, we believe a Trust but Verify approach that incorporates information-based oversight can absolutely complement a Zero Trust architecture. Trust but Verify has become increasingly important both due to the tremendous growth of unstructured information being generated and the wide variety of storage locations in use today (local hard drives, SharePoint, Google Drive, OneDrive, Box, etc.). Employees expect and, in some cases, demand access to information on their terms (for example, mobile devices, home workstations, public WIFI, etc.). Gimmal Discover provides information security teams with a tool capable of scanning many different types of content repositories using a wide variety of criteria (age, date, size, keyword terms, phrases, patterns, etc.), locate matching content, then take appropriate action (report, copy, move, delete). This type of functionality is helping our clients manage their valuable information resources in a variety of ways:
- Identify where personally identifiable information or content that poses a regulatory or litigation risk is stored
- Uncover confidential client information that may be improperly retained either through malfeasance or misfeasance
- Prompting data owners to review suspect information and indicate an appropriate disposition step (i.e., deletion, archiving, etc.), then applying the designated action
To learn more about how Gimmal’s tools can help you incorporate data as a foundational component of your information governance security model, please visit www.gimmal.com.
